As the pandemic forces many employees to work remotely, is your organization safe from a cyber security perspective?
Large and medium tech companies have mandated all employees to adopt a work-from-home policy. Many of these companies have the needed policies, infrastructure for remote connectivity and majority of employees are laptop users. There are many non-tech companies that are tech enabled and have the infrastructure for remote connectivity. However, their policies to work-from-home were either fluid or limited to a select few employees and/or contractors.
The unprecedented situation has forced companies to open up their infrastructure and applications for accommodating remote connectivity to all users, without the time to put in a lot of thought to understand the compromises. So, employees now will access many technologies remotely that were once accessible only form the inside. By exposing technologies that are considered internal to remote users there is a possibility of exposing the vulnerabilities associated with these technologies.
These past and coming weeks of remote connectivity is a perfect opportunity for threat actors to breach, steal data and/or implant back doors in organizations.
Vulnerable Technologies and your focus area(s)
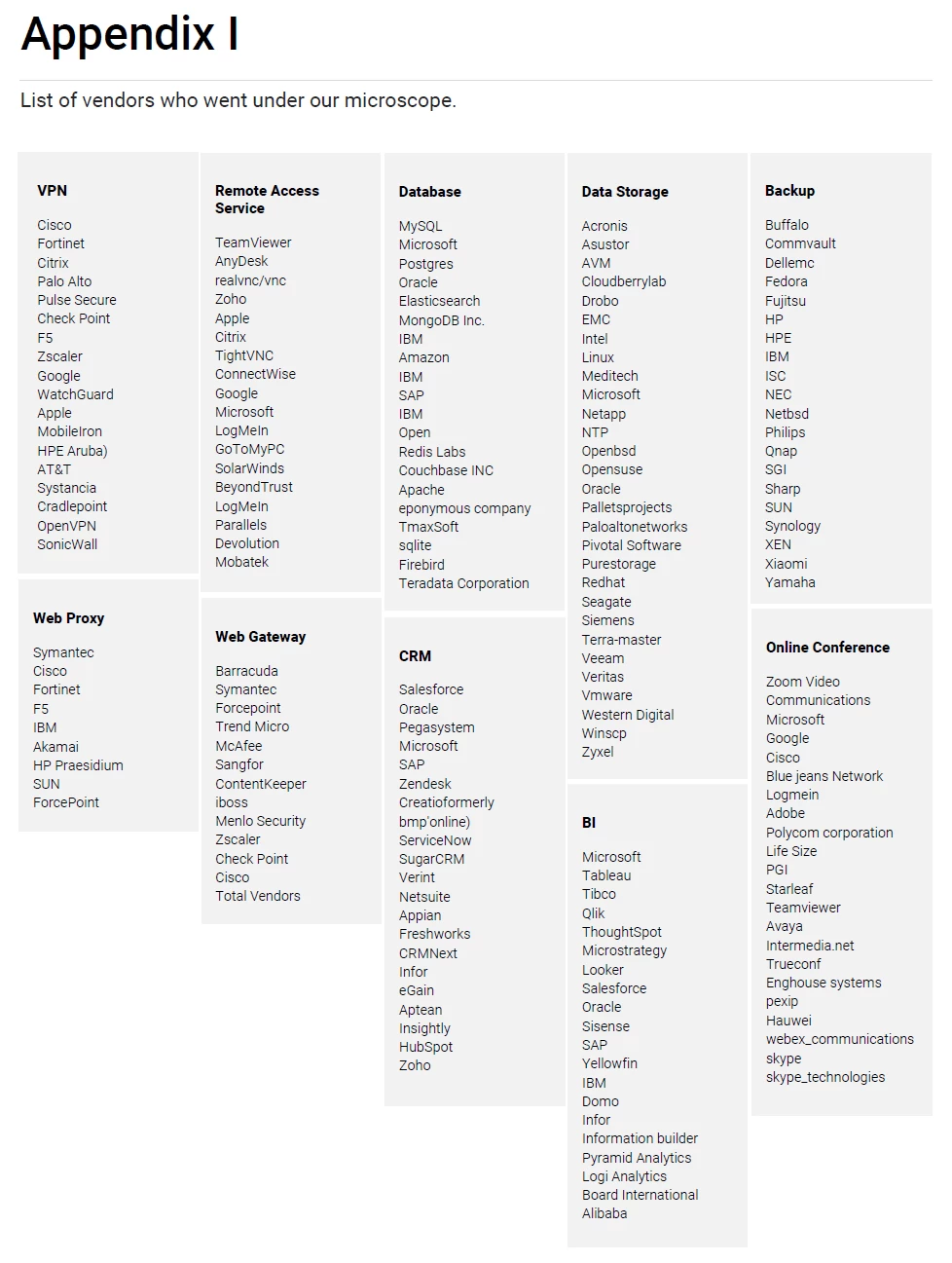
Across the world Governments and companies today are heavily dependent on technology for getting business done. They must have implemented most or at least a few of these products and solutions from leading vendors over the past decades. Each of these serves a specific purpose.
For this study we selected the leading vendors from Gartner and Forrester research. To view the list of all vendors who went under our microscope, please refer Appendix I.
Purpose of this report In this report,
we seek to highlight the vulnerable technologies and the CVEs undetected by scan solutions
1. Technology that has more weaponized vulnerabilities
2. Identify vulnerabilities that can be triggered remotely
3. Rate of weaponization over the last few years
4. Prioritizing vulnerabilities based on weaponization
5. Highlighting the quanta of exploitable vulnerabilities that go undetected [even by the industries' top scan solutions]
Overview of Vulnerabilities
The tech stacks listed in Figure 1 have been around for a long time and likewise have a long history of vulnerabilities. The earliest vulnerabilities (CVE) date back to 1999 from databases and backup-storage devices. The first VPN, Remote Access and Web Proxy vulnerabilities were seen in 2001 and 2002.
TWe analyzed 4,829 vulnerabilities spanning across all these technologies from 1999 through February of 2020 We further refined on the list of vulnerabilities that pose a real risk to an organization. We highlighted weaponized vulnerabilities for which exploit code exists that can take advantage of the vulnerability.
These vulnerabilities are of most importance to an organization. In general, most vulnerabilities are not weaponized, and this is true in analysis. Our research shows 543 out of 4,829 CVE entries being weaponized.
Vulnerabilities by Tech Stacks
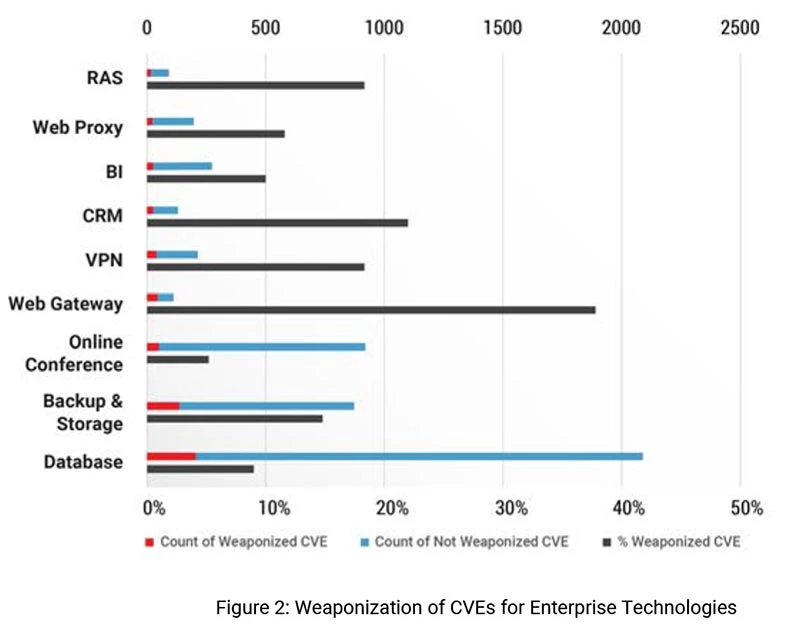
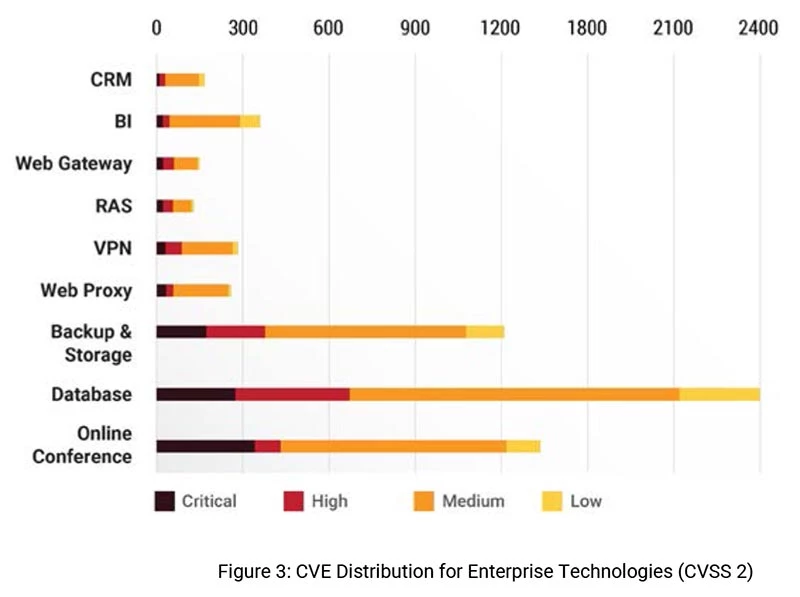
These results are interesting, when we compare the vulnerability trends seen across all technologies. Figure 2 shows that Database, Online Conference and Backup & Storage technologies have large number of vulnerabilities. However, when it comes to weaponization, the count in Database and Backup & Storage are the highest followed by Online Conference, Web Gateways and VPN's. Figure 3 shows the distribution of vulnerabilities based common Vulnerability Scoring System Version 2 (CVSS 2) assessment. Most number of critical and high vulnerabilities are from Online Conference, Databases and Backup & Storage technologies.
Vulnerabilities - Year over Year
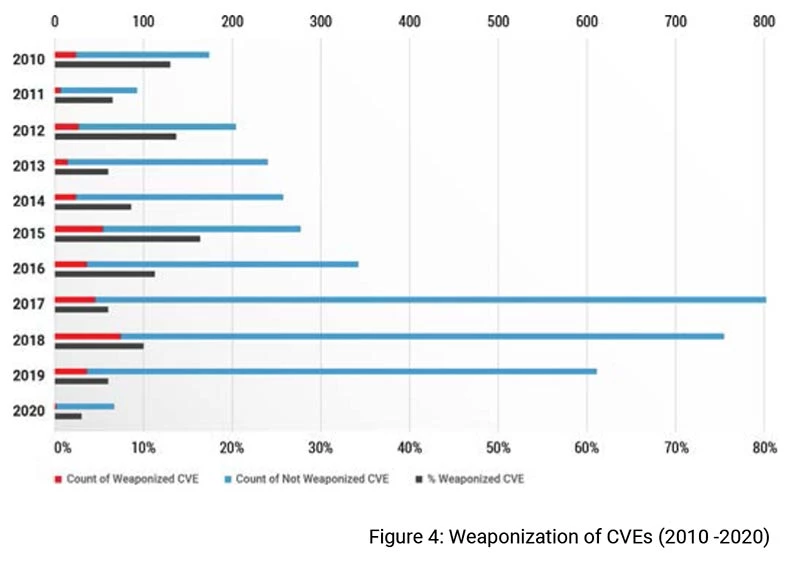
We next analyzed the dataset by the year in order to see how the weaponization of vulnerabilities has been changing year over year. Figure 4 shows each year broken by vulnerabilities that were weaponized versus those that were not. Data in 2020 only includes vulnerabilities through the end of February Here we can see that weaponization rates have increased considerably since 2015. The number of vulnerabilities discovered also increased steadily since 2015 and a pronounced spike in 2017.
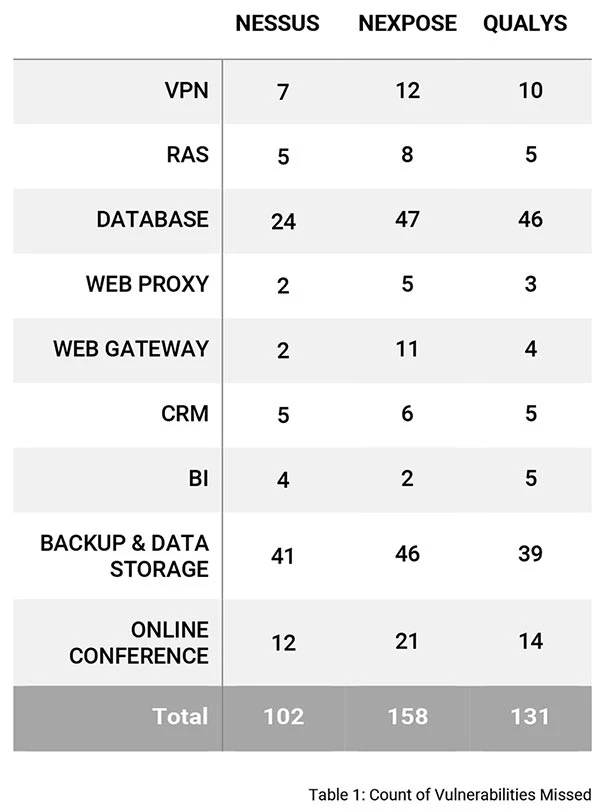
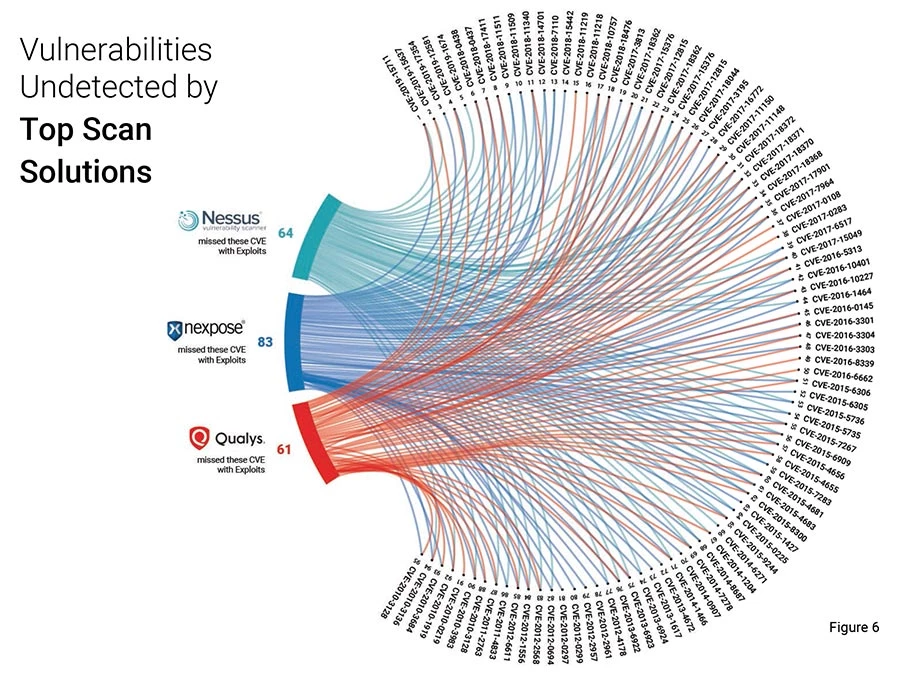
Vulnerabilities Missed by Scan Solutions
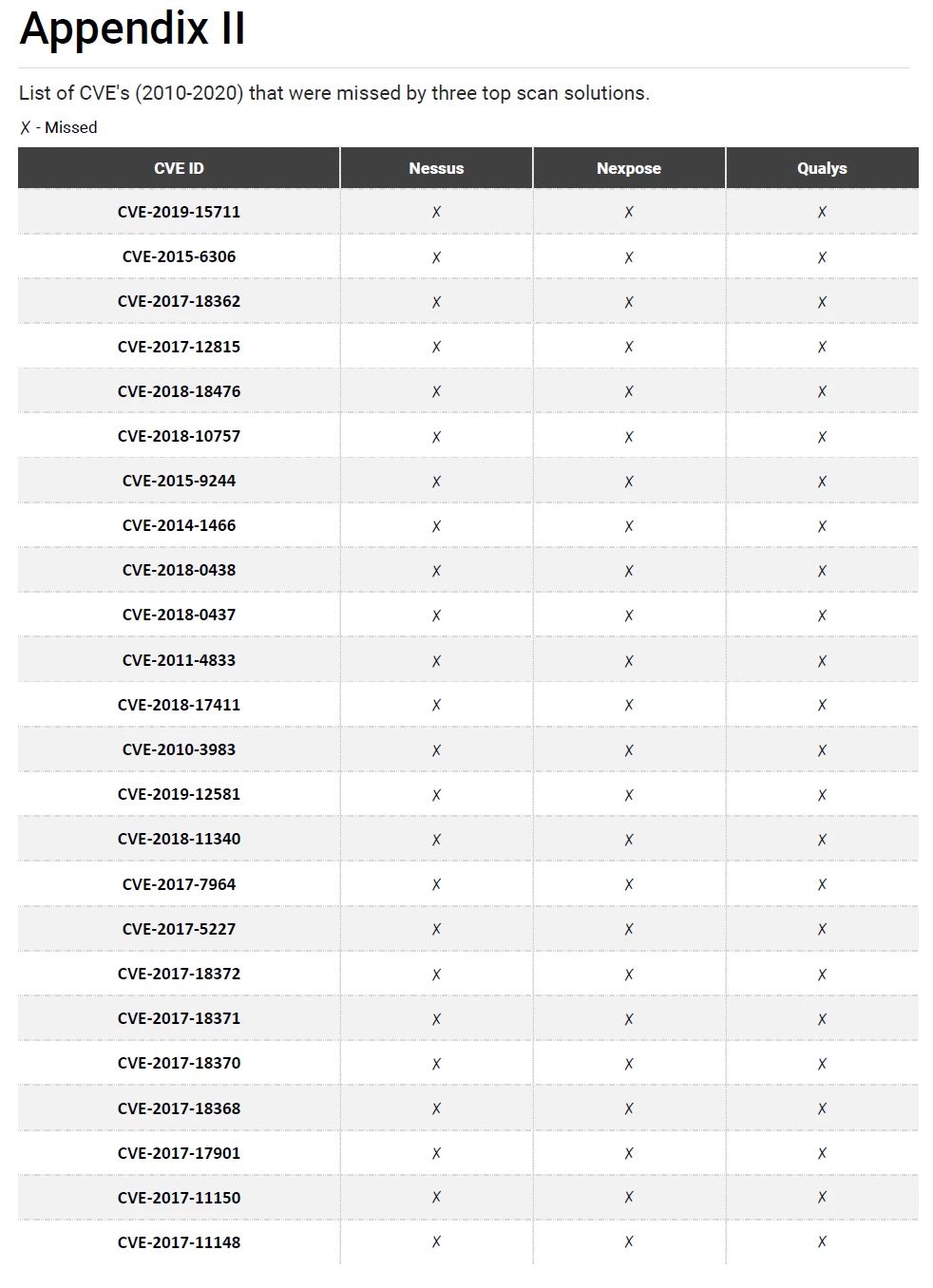
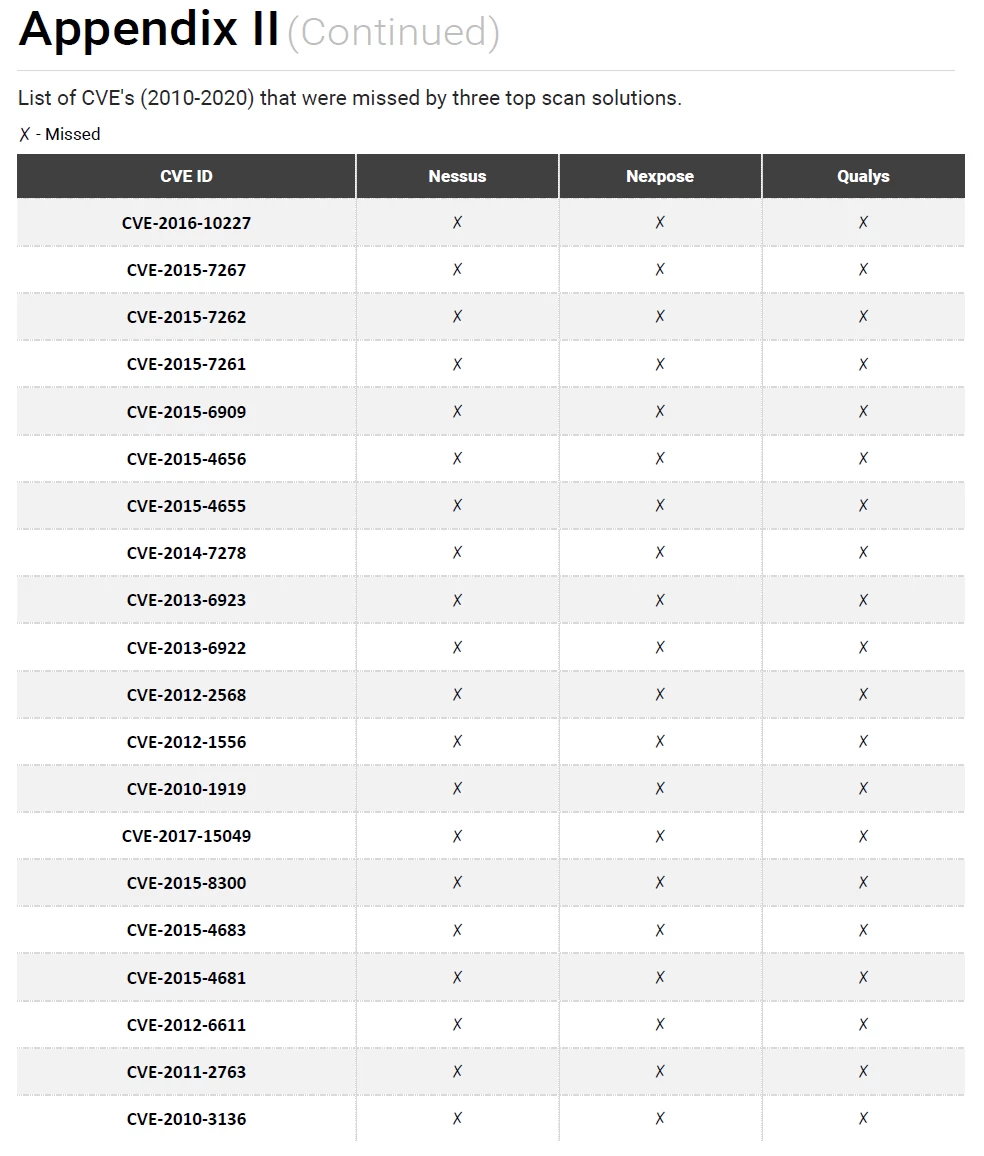
We analyzed the data further by comparing the CVEs with the plugins from some of the best scan solutions. It is very interesting to learn that the leading scan solutions fail to detect critical and high vulnerabilities that have weaponized exploits in the wild. Table 1 below shows the count of vulnerabilities from 1999 to 2020 that were missed by scanners. Chord diagram (Figure 6) shows the number of vulnerabilities from 2010 to 2020, that were missed by the scanners. To view the list of undetected CVES, please refer Appendix II.
Vulnerability Prioritization by Weaponization
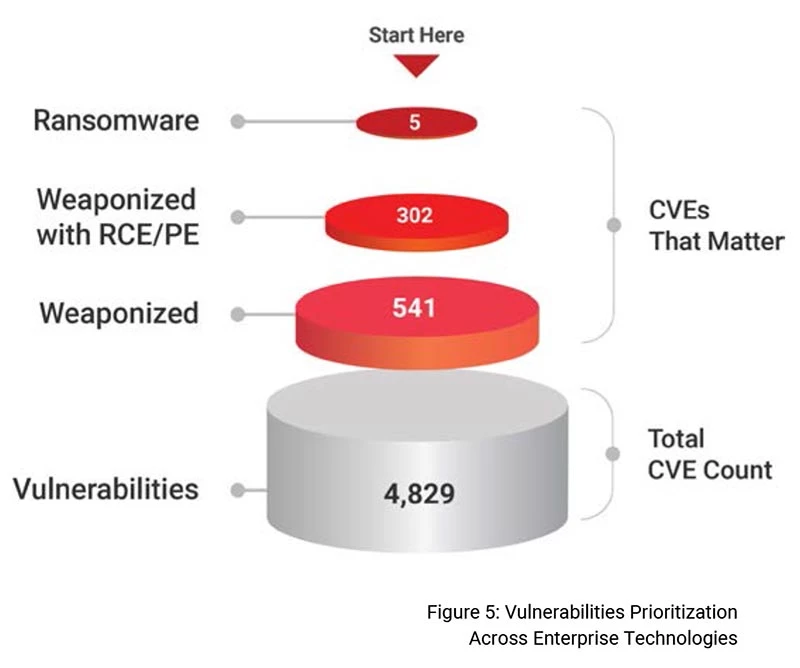
We further analyzed the vulnerabilities that are of high impact, those that enabled remote code execution (RCE), privilege escalation (PE) and/or an association with a known Ransomware.
We found 201 vulnerabilities enabled remote code execution, 103 vulnerabilities enabled privilege escalation and five (5) vulnerabilities linked to a known Ransomware. All RCE and PE capable vulnerabilities are weaponized. Figure 1 below shows that security teams should first focus on Ransomware, RCE and PE related vulnerabilities.
Conclusion
In this report we have seen the vulnerabilities of various enterprise technologies, and the impact they can have on the security of an organization. Not all organizations scan 100% of their internal assets; even if they did the probability of upgrading or patching is low for various reasons. Some of the reasons could be arduous and potentially risky as it may cause downtime or backward compatibility issue or failure of a legacy system, often lead by a "if it's not broken, don't fix it" mentality.
In these cases, it is critical that IT administrators have clear insight into the real-world risk of vulnerabilities during this pandemic. These internal assets never needed connectivity from the outside (to a remote employee), so they were safe. Because of COVID-19, all employees (100%) have been asked to work-fromhome. In order to accommodate all employees, IT administrators may have opened up or modified permissions for allowing access to these technologies (remotely). This is the perfect opportunity for threat actors to gain access by leveraging a combination of vulnerabilities across these technologies, which were considered secure few weeks ago.
This makes it particularly important for CISO's and security teams to be aware that 100% scanning of assets is not an option any more. If not done, such decisions can ultimately impact the security of the applications, databases, backups and the organization itself. IT teams shouldn't conflate the lack of weaponization with safety. Other technologies relatively show low weaponization, yet have relatively high numbers of vulnerabilities overall, which carry potential risk for the organization.
Ultimately organizations should have a good understanding of the overall attack surface of the various technologies, and the specific weaknesses that they contain. To achieve this an organization must implement a continuous scanning program across 100% of their internal assets.